Streamline data security management in Dynamics 365
Easily manage data security setup and maintenance, prevent data misuse, and ensure audit compliance with STAEDEAN’s Data Security Solution (an essential component of our Data Integration & Security Solution), embedded in Microsoft Dynamics 365 Finance & Supply Chain Management (D365 F&SCM).
Our enterprise-ready, no-code solution can help you:
- Achieve flexible segregation of duties, privileges, and entry points in D365
- Perform comprehensive security audits to help you prove your compliance
- Gain insights into non-compliant roles and users in D365 F&SCM
Book a demo to experience our solution in action
Benefits of Data Security Solution for Dynamics 365 F&SCM
Key Features of Data Security Solution for D365 F&SCM
Scroll to
Role-based Security Management
Enable scenario-based role creation and modify existing roles, as necessary, by recording the user's business processes and matching these to the required roles, duties, and privileges with necessary access levels.
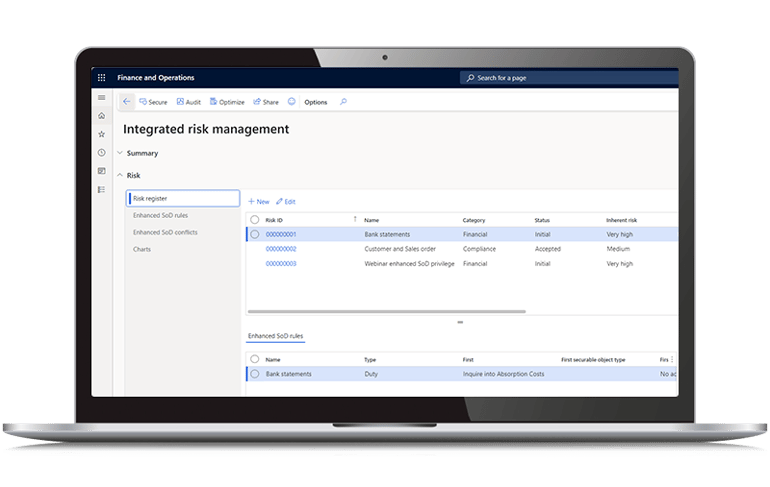
Flexible Segregation of Duties
Achieve flexible Segregation of Duties (SoD), Privileges, and Entry Points and define SoD violation rules, not only at the role level, but also at duty, privilege, and entry point levels, by creating a risk register and linking those risks with the SoD rules in D365.
.png?width=770&height=487&name=Flexible-Segregation-of-Duties-(SoD).png)
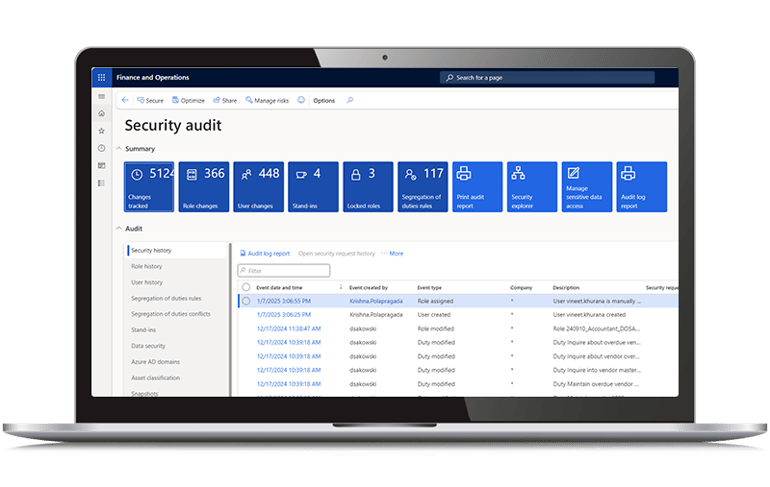
Comprehensive Audit Logs
Reduce time on internal IT audits and ensure audit compliance by leveraging our solution’s detailed audit logs, which include security audit, security user log, sensitive data log, stand-in logs, and user continuous logs.